Remote Work operations have led to a rise in cyber-attacks, both in terms of volume and sophistication previously unseen.
According to a recent report by Ponemon Institute and IBM, the average cost of a data breach is $3.86 million.
The need for anywhere-anytime access is making enterprise networks vulnerable.
What’s worse is that even if your own network is secure, threats can trickle in through backdoors built into the networks of your suppliers and vendors.
Enterprise security today is truly fraught with complexities.
Hackers, as usual, are five steps ahead of businesses in taking advantage of a situation that companies are still struggling to get a grasp over with all its inherent uncertainties. This has resulted in highly advanced attacks across dispersed networks of businesses with phishing schemes and social engineering-based strategies.
If there is one North Star of truth that businesses can take away from the current situation it’s that they would do well to assume a worst-case scenario for cybersecurity risks at all times.
Traditional security barriers such as firewalls and web gateways are no help at keeping threats like malware and ransomware away.
The need of the moment is to factor in network resilience in the very design of an organization’s network architecture. This is where the model of ‘Zero Trust Security’ can literally save the bacon for businesses. That’s why 80% of Organizations Plan to Adopt Zero-Trust Security Strategy in a 2021 survey!
What is Zero Trust Security?
Zero trust security uses strict identity verification for every account (person and device) that requests network access – irrespective of whether they are located inside or outside the boundaries of the network perimeter.
Zero Trust Architecture (ZTA) is free from specific technologies. It is simply a holistic approach towards maintaining network integrity that makes use of various technological principles and technologies.
Zero Trust security model considers each access request as a breach and verifies it as it came from an open network. Irrespective of where the request comes from or what assets it accesses, every access request is thoroughly authenticated, authorized, and scrutinized for anomalies before granting permission. It applies the least privileged access principles to reduce the threat landscape.
Key ‘Zero Trust’ Principles:
a) Verify Thoroughly
b) Grant Least Privileged Access
c) Assume Breach
This is a far cry from the traditional concept of securing perimeters around private networks using endpoint-based controls, such as approved IP addresses, ports, and protocols to recognize a list of approved applications, data, and/or users that are ‘trusted’.
If the integrity of one of these trusted resources is compromised, it translates to a free reign for the malicious program inside the network.
Features of Zero Trust Security
What makes zero trust philosophy unique is its recognition of a reality wherein attackers can be lurking anywhere – both within and outside of the network.
This makes it necessary for users and machines to be validated each time they request network access, so their integrity is always checked prior to access.
Zero trust security also relies on least-privilege access. Users will have access only to those resources that they may logically need in the course of fulfilling their duties.
Information is accessible on a strictly need-to-know basis. This effectively minimizes an individual user’s exposure to more sensitive parts of the network.
Another feature of zero trust networks is the concept of micro-segmentation. In essence, this refers to the practice of chunking security perimeters into smaller zones so as to maintain discrete access for distinct parts of the network.
In addition, multi-factor authentication (MFA) also acts as a core part of zero trust security. Managed IT Services can help in implementing zero trust architecture in business networks.
Zero Trust modeling relies on continuous monitoring, inspection, and logging of traffic and activities. They also rely on building user account baselines in order to track abnormal behavior that can hide malicious activity.
With automation in the offing, zero trust principles become highly accessible to implement in practice so it can perform efficiently and remain cost-effective for security teams.
ALSO READ: Compliance and Regulatory Consulting Services
Benefits of Zero Trust for Business and Security
-
Reduces Business and Organizational Risk
At its core, zero trust implicitly assumes all applications and services are hostile unless proven to be reliable through strict identity attributes. These security attributes are often immutable properties of programs that are used to meet predefined authentication requirements. Because zero trust operates on baseline standards of activity – any deviation is automatically triggered and analyzed for potential malicious activity. It also enables a high degree of transparency as it makes clear how assets within a network communicate. This enables a significant overall reduction in risk exposure.
-
Provides Control Over Cloud Environments
Despite considerable improvements in cloud security posture over the last few years, there is no denying that cloud migration sparks legitimate fears about loss of visibility and access control. Workload security continues to be a shared responsibility between the CSP and businesses. With a Zero Trust Architecture (ZTA) in place, security policies get established based on the identity attributes of communicating workloads and the project itself. This renders security independent of vulnerable network constructs, such as IP addresses, ports, and protocols. This results in protection throughout the journey of the workload and remains untarnished even as the environment changes.
-
Lowers Breach Potential
Apart from obvious financial losses, data breaches can also result in an immeasurable impact on customer trust in companies. Both customers and governments are demanding data privacy and security. Therefore, businesses need to meet that obligation in the best possible way. To reduce breach potential, the network using Zero Trust architecture continuously analyzes workloads via their intended states. The moment there is a mismatch, its communication privileges are cut off from the rest of the system. It’s a form of practicing automatic distrust by the system until there is adequate course correction as dictated by system policies.
-
Boosts Compliance and Improves Trust
Zero trust architectures inherently work to improve the IT audit and compliance adherence capability of a system. Consider getting in touch with cybersecurity consulting services to improve your IT audit and compliance adherence frameworks.
Building Zero Trust into Your Organization
A Zero Trust security model must cover the organization’s entire digital landscape and serve as an Integrated Security Approach (ISA) and end-to-end strategy.
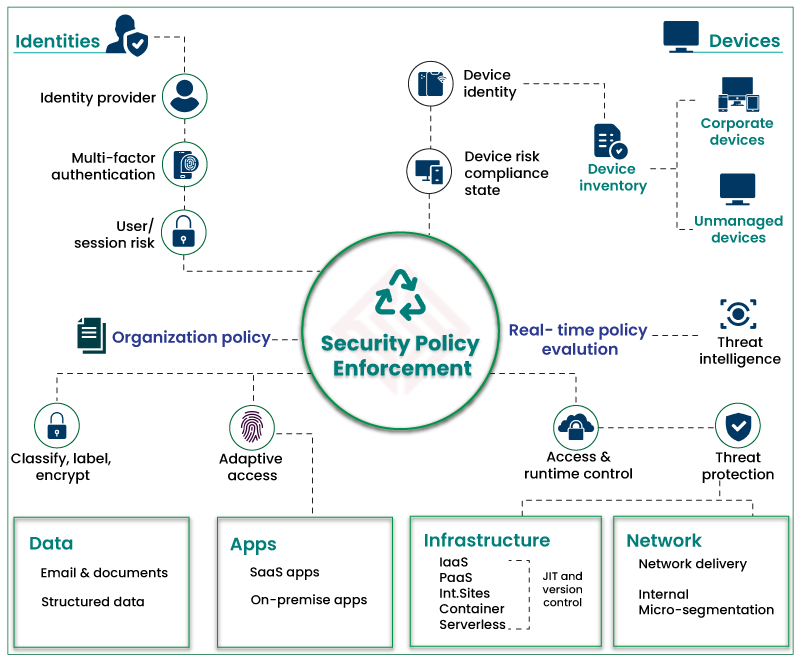
This can be accomplished by enforcing Zero Trust procedures and processes across six key elements, namely, Identities, Data, Devices, Applications, Infrastructure, and Networks.
1) Identities
Identities represent users, services, systems, or remote devices. Whenever an identity requests access permission, verify and secure the identity with robust authentication across your digital landscape. Access must be compliant and abide by the least privileged access policy.
2) Devices
Once a user gains access to an enterprise asset, data can transfer to a host of devices, from on-premises workloads to cloud servers and corporate systems to vendor devices. As this distributed data creates a widespread attack surface, organizations must monitor and implement device health and compliance before granting access.
3) Applications
Applications and Application Programming Interfaces (APIs) can be traditional on-premises, modern cloud-native workloads, or SaaS applications. Organizations must enforce controls and technologies to confirm proper in-app permissions, check for anomalous behavior, monitor user actions, and authorize appropriate configuration options.
4) Data
Organizations must shift from perimeter-based data protection to data-driven protection. Use intelligence to categorize, label, and encrypt data and control access based on organizational policies.
5) Infrastructure
IT Infrastructure, including on-premises servers, Virtual Machines (VMs), or containers, are prime targets for cybercrime. Organizations must rely on telemetry to identify attacks and vulnerabilities, automatically restrict and block abnormal behavior, and implement the least privileged access policy.
6) Network
Organizations shouldn’t trust users and devices just because they are on the internal network. Implement network controls to improve visibility and prevent threats from spreading across the network. Employ end-to-end encryption, real-time threat detection, and network micro-segmentation.
In Conclusion
Though a Zero Trust security model is most effective when implemented across the organizational digital ecosystem, companies can take a phased approach based on the current cybersecurity maturity, available resources, and business objectives. It’s imperative to consider each investment carefully and align them with the present business needs.
Post Courtesy: Sam Goh
More Articles:

