Privileged Access Management (PAM) solutions help organizations manage their privileged accounts to secure their critical assets, stay compliant, and prevent data breaches.
Modern-day organizations face an array of challenges when securing the business from the risks of potential misuse of privileged accounts. Cybercriminals regularly target these privileged accounts to infiltrate critical information or inflict damage to an organization.
Therefore, the protection and management of privileged accounts are imperative to securing valuable information and protecting brand reputation.
What is Privileged Access Management (PAM)?
‘Privileged access’ is all about access to critical assets, including computers, networks, software applications, and other digital devices. Thus, Privileged Access Management (PAM) refers to the class of tools, systems, technologies, and solutions used to secure, monitor, and control access to an organization’s sensitive information and critical assets.
Why do Organizations Need PAM Services and Solutions?
Privileged accounts host users such as c-suite executives, business managers, and administrators with the highest level of access and control over networked devices, databases, applications, and servers.
Hence, privileged accounts must be managed and controlled with the utmost care as they are the gateway to an organization’s most critical assets.
However, many enterprises grapple with privileged access management for several reasons, including:
- Human error or negligence that improperly provides privileged access to ineligible or unauthorized employees.
- Technology sprawl and excessively complex IT infrastructure make it resource-intensive and time-consuming to manage privileged access.
- Shortage of expertise to effectively manage a PAM system.
- Relying on manually-intensive, error-prone processes to manage privileged accounts increases costs and risks.
- Lack of tools and processes that effectively manage and audit privileged accounts, exposing the business to security threats and compliance risks.
A perfect privileged access management service provider can effectively address the above and many such concerns to secure privileged accounts.
How Can StealthLabs Help?
StealthLabs believes that proactive preparation and constant monitoring are the best ways to secure privileged accounts. We know that developing and handling an in-house security operations center to oversee this task can be resource-intensive and time-consuming.
This is where StealthLabs can help!
Our skilled Privileged Access Management (PAM) team works with you to develop your PAM strategy, solutions, and procedures to enable you to protect and control privileged accounts, as well as identify and respond to privileged account threats.
What’s Different About StealthLabs?
StealthLabs’ Privileged Access Management (PAM) service helps you control the use of administrative privileges to secure access to your most valuable assets effectively. Our fully managed, end-to-end PAM solution narrows the attack surface associated with your organization’s privileged accounts and helps you demonstrate compliance.
Our skilled PAM team works with you to:
1) Discover Privileged Accounts
Identify privileged accounts across your IT infrastructure, which assets they can access, and which are most critical to the business. Then, we help you secure, control, manage, and monitor these privileged accounts and credentials.
2) Configure and Customize Solution
Design and configure the PAM solution on par with your business needs. We can install and configure your PAM solution to implement the least privilege policies and secure privileged accounts.
3) Administer Privileged Accounts
Administer the privileged accounts when new systems or users are added, manage the lifecycle of privileged accounts, and formulate password policies.
4) Audit and Report
Our PAM service provides you with detailed auditing and reporting of account activity and user behavior around the clock, so you will never be in the dark about the activity taking place on your network.
Our PAM Capabilities
SteathLabs provides secure privileged access management solutions wherever your systems operate, whether in on-premise data centers, the public cloud, the private cloud, or the hybrid cloud. We not only provide higher levels of security but with significantly less delay and expense.
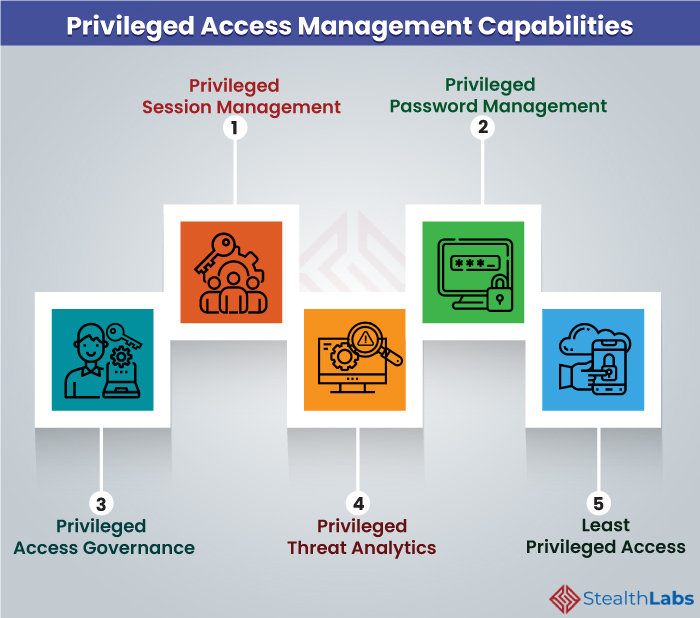
Our PAM capabilities include:
1) Privileged Session Management
Control, monitor, and record all sessions of administrators, users, systems, and applications that involve privileged access and permissions. It tracks and creates an audit trail of actions that occurred during a privileged account session.
2) Privileged Password Management
Control and secure the process of providing privileged password credentials and enforcing password policies. It enables regular rotation and revocation of passwords while maintaining them in a centralized and encrypted vault.
3) Privileged Access Governance
Establish a unified governance approach for all employees, irrespective of their role and access privileges. Users can request privileged or general access permission, and administrators can enable or disable access from a single portal.
4) Privileged Threat Analytics
Identify high-risk privileged users by analyzing privileged account sessions. Monitor suspicious user behavior and other irregularities in order to identify internal and external threats and take immediate actions to prevent breaches.
5) Least Privileged Access
Provide the right access to the right administrators so that they can perform their duties. Take a least-privileged security approach with a granular delegation of administrative access.
Benefits of Privileged Access Management from StealthLabs
As a critical aspect of cybersecurity management, PAM solutions and services offer a wide range of business benefits, including:
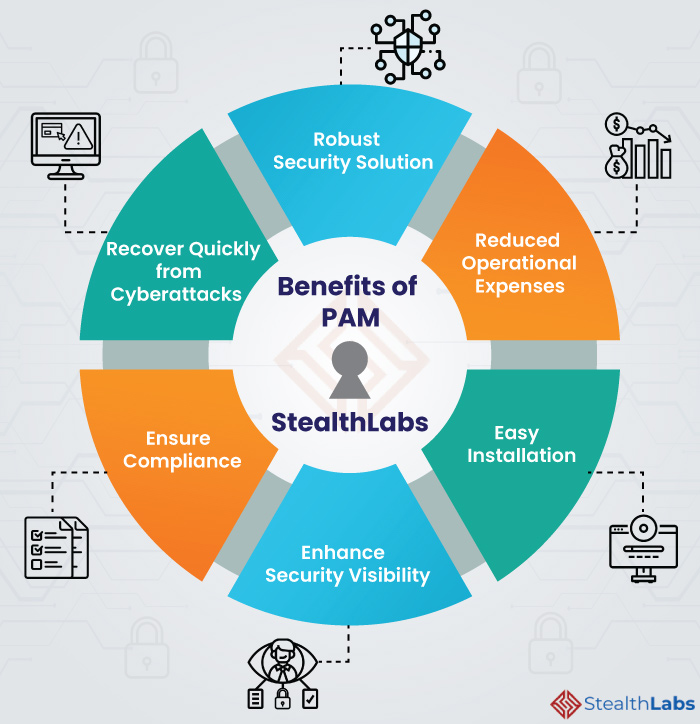
1) Robust Security Solution
PAM is a robust security solution that can help improve insights into vulnerability assessments, IT network scanning, access management, and identity governance, among others. This improvement in cybersecurity serves as a deterrence to malicious actors.
2) Reduced Operational Expenses
Reduce operational expenses by eliminating manually intensive, time-consuming, and error-prone administrative processes. This simplifies operations and improves IT security teams’ efficiency, freeing valuable staff to focus on core business activities.
3) Easy Installation
Enable fast, straightforward installations by eliminating the need for your team to manually deploy and configure a complex PAM solution in-house.
4) Enhance Security Visibility
PAM solutions help you identify privileged accounts and who has access to them, implement well-informed privileged account security policies, and monitor activity on privileged accounts.
5) Ensure Compliance
With robust security management recommendations, PAM develops a strong baseline of policies that can help comply with industry and government regulations.
6) Recover Quickly from Cyberattacks
PAM solution enables you to quickly audit recently used privileged accounts, identify passwords that have been changed, and track applications that have been executed.
How is PAM Different from Identity and Access Management (IAM)?
Privileged access management and identity access management are often considered the same, as they both deal with users, access, and roles. However, there are some distinct differences between them.
PAM Vs. IAM
| Privileged Access Management | Identity Access Management |
| Focuses on managing administrative and privileged users | Focuses on authenticating and authorizing general users |
| Users will have access to a larger number of privileged accounts and business and technical functions | Users will have access to a low number of business-specific applications |
| Limited standard protocols | Large ecosystem of protocols and authentication mechanism to secure identities |
| Covers smaller attack surface | Covers large attack surface of access from users across the organization |
Why StealthLabs?
StealthLabs is one of the leading cyber security companies in Texas, USA. Our highly-skilled teams combine market-leading technology with experience and knowledge of cybersecurity to provide context-rich analysis to our customers.
You can reach out to us for more information about building cyber resilience with Privileged Access Management (PAM).
Related Cybersecurity News:

