Data Security Vs Data Privacy: An Imperative Distinction to Protect Data
In the present digital world, organizations face a multitude of challenges related to the privacy and security of employee, consumer, and client data.
The sheer volumes of data that enterprises handle and store is growing and drive a greater need for data protection practices. In addition, computing environments have become highly complex, routinely spanning the cloud, the enterprise data center, and numerous devices ranging from IoT sensors to remote servers.
This complexity proliferates the attack surface, making it more challenging for organizations to monitor and secure data.
Therefore, it has become crucial for organizations to incorporate data security and data privacy policies into a sound data governance strategy to prevent data breaches and achieve legal compliance.
However, many organizations believe that their data security policy covers data privacy and vice versa. They often use data security and data privacy interchangeably.
But this is not the case. There are distinct differences between data security and data privacy.
What’s the Core Difference Between Data Security and Data Privacy?

Data Security is commonly referred to as confidentiality, availability, and integrity of information. It is all about the practices and procedures that focus on protecting personal information from unauthorized access, data breaches, cyberattacks, and accidental or intentional data loss. Data security ensures that data is accurate and reliable and is available for authorized users.
A data security plan includes resilient data storage technologies, encryption solutions, data erasure, data masking, physical and logical access controls, breach response, and multi-factor authentication.
Whereas Data Privacy is concerned with the procedures and policies that govern the collection, storage, sharing, and usage of Personally Identifiable Information (PII) and proprietary corporate information. It refers to the rules and regulations that ensure personal or private information is being controlled on par with the preferences of the concerned individual(s).
Now, data privacy laws like GDPR, CCPA, and HIPAA impose a broader set of privacy standards and regulatory compliance requirements on companies that store or process the PII. These laws can impose penalties or even criminal charges for failure to safeguard the privacy of PII and other highly sensitive personal information.
Understanding the Distinction: Data Security Vs Data Privacy
The best way to understand the distinction between data security and data privacy is to consider the mechanisms used in both cases. An organization may have effective and robust data security, yet the procedure or process that collects or handle information might violate the privacy policy.
For instance, an organization might ensure data security by encrypting, masking, and properly accessing the data. But if it gathers that information improperly, for instance, without any proper consent from the concerned individual, the organization has violated data privacy requirements even though data security remains unbreached.
Therefore, organizations must understand that data security can be possible without data privacy. However, data privacy cannot be achieved without data security.
Data security is a prerequisite to data privacy.
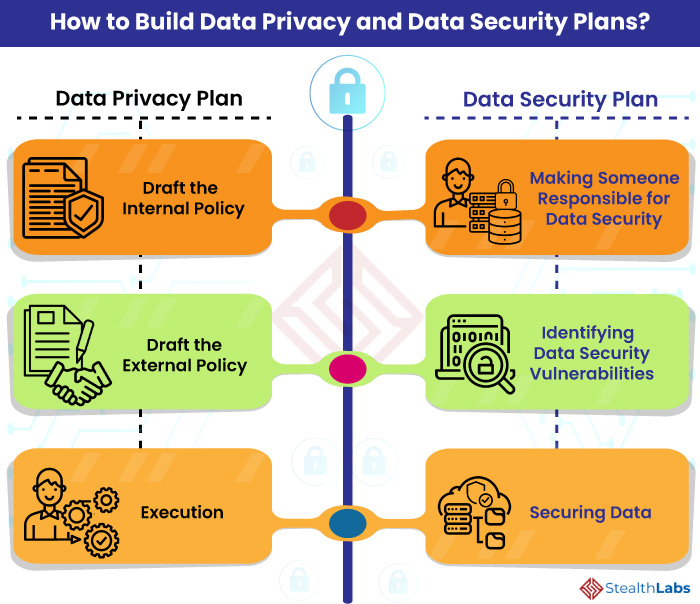
How to Build Data Privacy and Data Security Plans?
Concerns and losses of personal information and sensitive data can lead to business interruption, significant reputational damage, and regulatory penalties. Organizations can check unforeseen business interruptions by deploying good security practices and conforming to the associated privacy requirements.
Developing a Data Privacy Plan:
The value and volume of data are growing exponentially, as a result, data privacy has emerged as a board-level issue and a competitive advantage, apart from being a compliance requirement.
A robust data privacy plan needs both internal and external policy. While the external policy informs clients, customers, and shareholders about what kind of data the organization is collecting and why, the internal privacy policy defines what the company and the employees can do with that information.
1) Draft the Internal Policy
Firstly, the organization should thoroughly gather information about what data they need to collect.
Secondly, draft an organization-level comprehensive policy that outlines what kind of data is being collected, who is responsible for executing the policy, and the related information of the actual data laws, to keep every employee on the same page.
Lastly, take stock of all the collected data and develop a comprehensive inventory. Identity data owners or who have access to the data and monitor the flow of data.
2) Draft the External Policy
Firstly, organizations should identify all the laws and regulations pertaining to their business and location. A legal adviser who specializes in your industry can help you with it.
Frame a privacy message that outlines what data the organization is collecting and why, on par with the legal requirements. Copying from the privacy forms of other companies in your industry could be a good start, but work with your legal adviser to ensure that your privacy statements are on par with your organization’s practices.
3) Execution
Organizations need a multi-pronged approach to broadcast and execute the internal and external privacy policy.
The internal privacy policy should be made accessible to all the relevant employees, and the employees must be trained on the new policy. Also, the developers should deploy the new privacy changes throughout the system.
The external privacy policy should be available on the website, a mobile app, on paper forms, or wherever the customers and clients see it.
Developing a Data Security Plan:
A comprehensive data security plan should help the organization address the growing challenges inherent in securing today’s complex computing environments. It includes understanding where the data is stored, tracking who has access to it, and preventing malicious activities and suspicious file movements.
A data protection plan that enables enterprises to tackle structured, as well as unstructured data, can simplify the task.
Structured data is the information that is highly organized and formatted, making it easy for the organization to collect, process, and analyze it. For instance, the kind of information you find in your Identity and Access Management (IAM) system is structured data.
Whereas unstructured data is information that is not organized in a pre-defined manner, making it difficult to process and analyze. For example, emails, texts, voice recordings, PowerPoint decks, paper notes, printouts, and USB dongles.
1) Making Someone Responsible for Data Security
Organizations should employ a Chief Data Officer (CDO) or designated information security professional to oversee their data processes and compliance and ensure that training is up to date and available regularly to the employees.
2) Identifying Data Security Vulnerabilities
Organizations need to assess and address their vulnerabilities before cybercriminals use the flaws as an entry point into the system.
Three basic steps to identify vulnerabilities in data security are penetration tests, auditing, and software solutions.
3) Securing Data
The organization’s plan to secure data should take both structured and unstructured data into account.
Securing structured data starts with:
- Creating secure, central storage for data
- Tracking data entry and usage
- Implementing multi-factor authentication and single sign-on policies
- Protecting devices with secure passwords
- Training employees
Securing unstructured data starts with implementing a robust Data Loss Prevention (DLP) plan to identify the most sensitive unstructured data. Then, find the users who are collecting and modifying that data and make them responsible for its security.
Moreover, train and educate employees about the risk of USB drives, sensitive information written on paper, and mobile phone photos and videos.
How StealthLabs Help with Data Privacy and Security?
As data becomes more valuable and vulnerable, data security and privacy needs have outmatched most organizations’ expertise, skills, and technologies. As a result, data protection demands often surpass available organizational resources.
That’s why it’s crucial for organizations to make a move to the managed cyber security solution.
We provide cybersecurity as a service. With years of industry presence and strong domain expertise, we can help your business with new data risks and opportunities.
Our portfolio of Information Security services includes:
- Compliance Advisory Services
- Identity and Access Management Services
- ITSM Incident Management Services
- Managed IT Security Services
Let’s Talk!
More Information Security Articles:
- 25 Scary Data Breaches that Shook the World in 2020
- Steps to Create An Information Security Program Plan
- Telemedicine and Cybersecurity: Securing Health Data!
- US Cybersecurity: 64% Americans Don’t Have Data Breach Response Plan
- Infographic – Cybersecurity Myths Vs Reality
- Top 16 Cybersecurity Myths and Misconceptions Worth Knowing!
- Top mobile security threats you can protect yourself from