Internet of Things (IoT) is one of the innovations driving the world. With people wanting to synchronize their digital gadgets, what was a matter of convenience has become a core aspect of life. Be it at work or while at leisure, we love the devices being in sync as it wicks away a great deal of stress and increases personalization. At the business level, critical operations have become easy. From medical treatment to the construction sector, various industries use IoT to increase collaboration and stunt expenses.
However, the increased collaboration and complete synchronization have attracted the attention of threat actors as there are possible scenarios in which hacking one device would lend them access to various interlinked devices. Of course, one can embrace security measures to ward off such attacks, and in this blog, we shall look at those steps. But, first, let’s address whether IoT security is required in the first place.
Why Internet of Things (IoT) Security?
If one observes the technology adoption trend, mankind embraces the new technology in a very rushed manner. Due to the hype or curiosity, we don’t want to appreciate or understand the intricacies of securing the technology. The same is the case with IoT. With syncing and seamless collaboration amply projected, IoT was embraced rather hastily.
Useful Link: Top 5 Remote Work Cybersecurity Threats
The American Department of Homeland Security echoes the sentiment as it opined that IoT security is a top concern for the department. Additionally, research from 451 Research outlined the same aspect as 55% of its surveyed audience outpointed that 55% of IT professionals felt IoT security was a priority. So, without further ado, let’s look at the steps required to fortify your IoT setup.
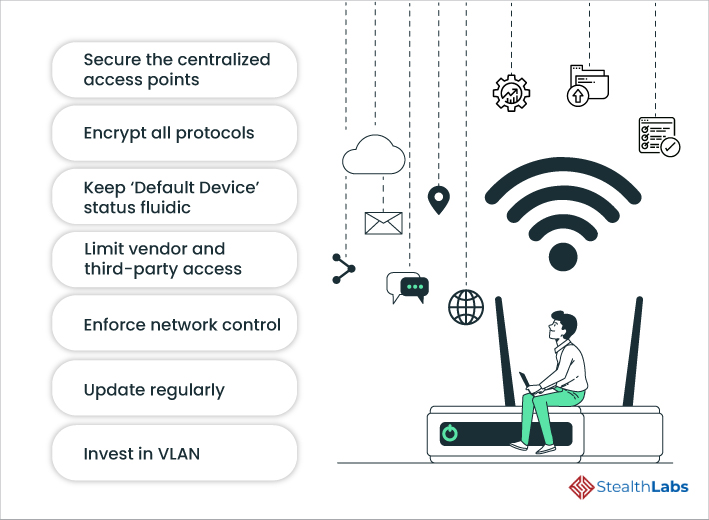
1) Secure the centralized access points
IoT means multiple access points, which indirectly means that anyone with the know-how can access the digital infrastructure. These multiple inlets are potential entry points for hackers if you don’t secure them. Therefore, it is wise to centralize access as it is a chore to monitor all the points. This centralized access lends you the scope to secure ingrain security wherever it is required. Additionally, monitoring the access node would become accessible as access information can be obtained without much effort.
2) Encrypt all protocols
In this age where every company is falling prey to hackers, encryption is the first line of defense you need to put up against cyberattacks. There will be innumerable protocols with IoT that dictate data management and operational control. Most businesses have already understood the importance of encryption and have implemented it in their protocols. Additionally, it doesn’t require much effort to implement this across the company.
3) Keep ‘Default Device’ status fluidic
Default devices are crucial from an operational standpoint. They lend ease of access and endow certain advantages. However, this default device should be swapped within the IoT devices to throw threat actors off the track. Keeping all the eggs in one basket is dangerous, and by swapping the default status, the company would be securing all the IoT networks by preventing unwanted access.
Useful Link: Passwordless Authentication: All You Need To Know!
4) Limit Vendor and Third-Party Access
Companies often rope in vendors to provide services and deliverables. However, this is an unintentional inlet for threat actors if the credentials are compromised. One ought to control the third-party access, which includes the vendors. This can be done by initiating MFA from a mobile phone or desktop app. Protocols must be established as to how and who will have access, and they should demarcate the level of access that third-party vendors will have. This is one of the zero-trust policies you need to embrace as soon as possible.
5) Enforce network control
Having a flexible network is liked by all, but such a network is porous and can let in malware. Therefore, it is wise to integrate network access software with IoT infrastructure, eliminating the potential of a network breach. One can use vulnerability scanners to scan the network for gaps if network access software affordability is a constraint to the organization.
6) Update Regularly
Any static software tool is an easy target if the version is not changed for long. It only lends ample time for the threat actors to study the software for gaps. So, it’s wise to update regularly and ensure all the IoT devices are updated. Any obsolete IoT device is a potential Achilles heel. It is better to automate the software update implementation across the infrastructure as it stunts the chances of a breach.
Useful Link: How small businesses can fend off cyber attacks
7) Invest in VLAN
A corporate network is a preferred target as all IoT devices are on it. It is better to do away with the corporate network entirely and get a Virtual Local Area Network (VLAN). The VLAN provision allows the organization to enable individual connections to IoT and monitor the devices connected to the VLAN. This monitoring also gives the company statistics regarding IoT device usage.
Final Thoughts
IoT is a good productivity tool that holds immense potential. However, threat actors are everywhere, waiting for an opportunity to breach networks for their wanton gains. Countless attacks underscore the significance of hiring a security Partner such as StealthLabs. Experts at StealthLabs have secured and defended various clients by plugging the vulnerabilities.
So, reach out to StealthLabs and fortify your business.
Additional Resources:

