Why is Passwordless Authentication the future?
Typically, employees of an organization are obligated to create complex and unique passwords, remember them, and change them frequently. They are expected to remember around 10 to 30 different sets of usernames and passwords to perform their tasks. Making matters worse is that they must deal with quite a few digital accounts in their personal life.
This, inevitably, has led to the reuse of the same weak passwords, sticky notes filled with passwords, and frequent reliance on the ‘forgot password’ function. No wonder passwords have become a prime target for cyberattacks. According to a recent Verizon Data Breach Investigations Report, over 80% of data breaches are due to compromised passwords.
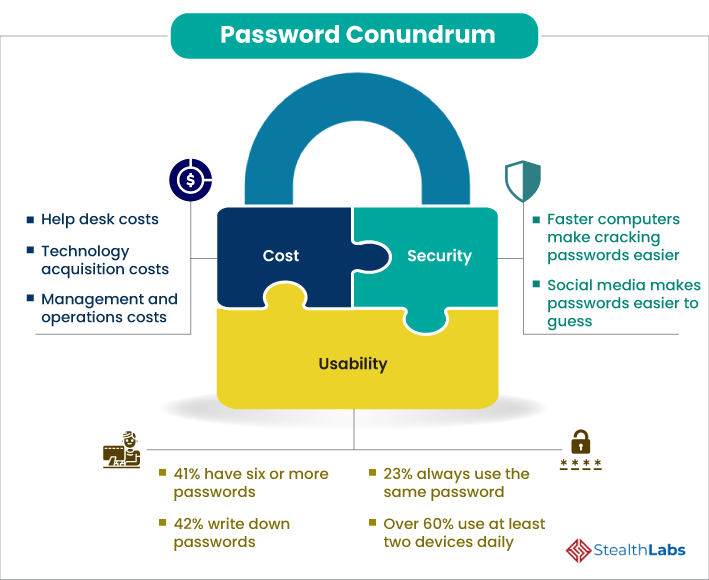
The Password Conundrum
- 23 percent of surveyed users always use the same password
- 42 percent of users write down passwords
- 20 percent of users routinely share passwords
- 56 percent of employees reuse passwords across personal and corporate accounts
Yet, for ages, passwords have been the most crucial security aspect. Fortunately, the passwordless future is here. The tech giant Microsoft is already leading the pack. The top IT company introduced passwordless sign-in for Microsoft accounts in September 2021.
Also Read: Understanding the Security Threats that Remote Working Poses
So, it’s time to bid adieu to gibberish passwords.
Let’s Go Passwordless!
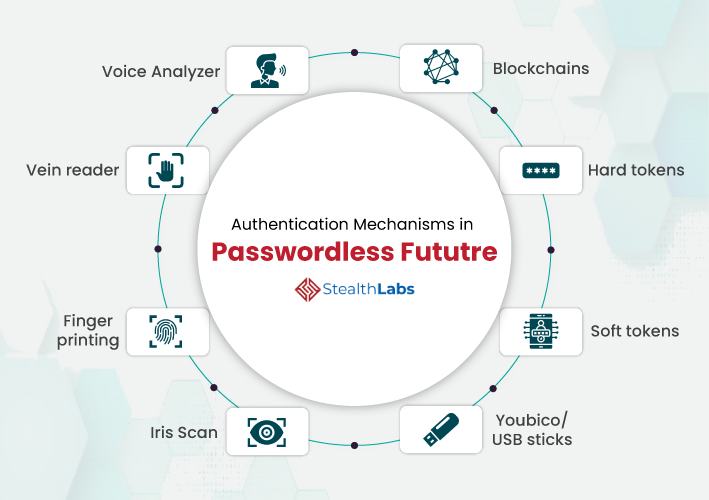
What Does Passwordless Authentication Mean?
First, let’s get cognizant of what passwordless is and isn’t and some passwordless myths. First off, passwordless isn’t multi-factor authentication. Nor is it single sign-on or the use of OTPs through SMS or email.
The passwordless model is all about basing identity verification on ‘possession factors’ that uniquely identify users. It can include a one-time password generator, a hard token, biometrics, or a registered mobile device. In a nutshell, passwordless authentication weeds out the problem of using weak passwords.
Also Read: How Can Companies Be More Resilient in the Face of Ransomware Threats?
For organizations, it eliminates the need to store passwords, leading to robust security, fewer attacks, and reduced IT support costs. For users, there’s no requirement to create, remember or store passwords, leading to a better user sign-in experience.
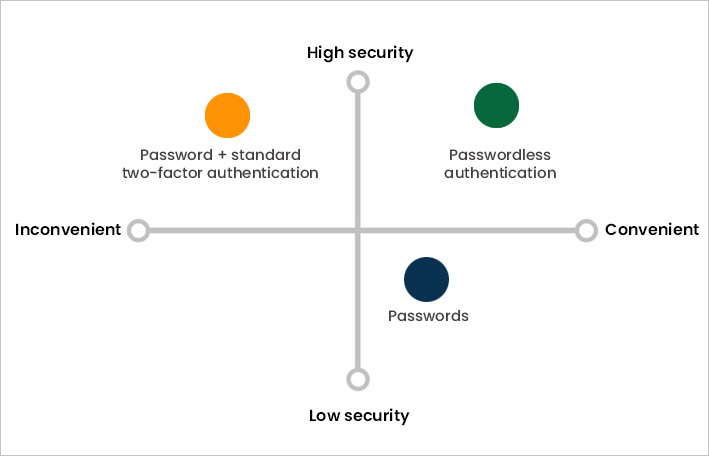
Passwordless Authentication Recommendations:
- Understand how the passwordless approach aligns with your operations flow. Then, make the required cultural and technical shifts to operate in this new authentical world.
- Assess your current digital identity capabilities and hammer out the roadmap. It must include how your organization authenticates the users through every channel.
- Collaborate with c-suite executives to define passwordless authentication and align it with the business objectives.
- Given the explosion of passwordless software vendors, it can be challenging to select the right vendor. Choose the one who can supplement and integrate your current digital identity capabilities and understand the roadmap.
- Dive deep into the process of managing the new authentication tokens and the device registration. Leverage automation to enable low-friction, high-reward processes.
- Integrate passwordless authentication with zero trust strategies to further boost the security posture.
Also Read: How small businesses can fend off cyber attacks
4 Strategies for Successful Passwordless Authentication
Along with the recommendations mentioned above, consider the following strategies for the successful implementation of passwordless authentication:
1) Set the Scene
Let the top management know how a passwordless model brings a high return on investments. Promote the benefits at the outset of the new initiative. Broach how passwordless authentication enables 3X times faster sign-in, fosters security, and enhances productivity. It is easy to get their enthusiastic buy-in when they understand that these methods deliver a high ROI.
2) Segment Users
The first and foremost step in passwordless authentication is to segment the users in your organization. Users must be categorized into two groups: 1) users in compliance boundary (for instance, users who handle customer PII), and 2) the other users.
This bifurcation is a must as some compliance requirements mandate the usage of usernames and passwords. Therefore, until the regulation adapts to the new authentication, the users in this segment must continue using passwords. However, the latter segment, which is probably quite large, can embark on the no-password journey.
You can further categorize the second segment based on risk exposure, such as high-risk communities, like c-suite executives or senior leadership, and those with privileged access, like IT administrators.
Once the users are segmented, configure authentication methods for each segment based on risk. Ensure that users get acquainted with the new sign-in method.
Also Read: Driverless Car Security Issues: Potential Cyber Threats!
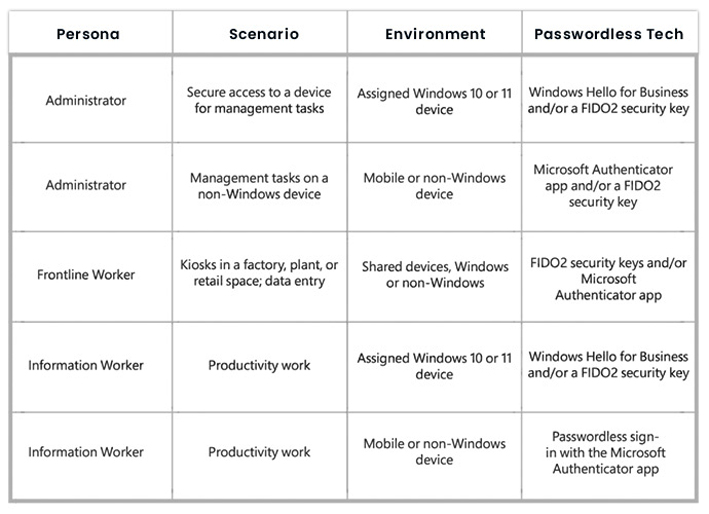
3) Select the Right Technology
Determine which passwordless technology suits best for each group of users while considering your level of flexibility. Below is a practical example by Microsoft on choosing which method will work best for each group:
4) Start Small
Adopting passwordless authentication doesn’t have to be an all-at-once approach. Start small with a few groups to introduce the new authentication method as an alternative to the legacy sign-in methods. This helps users adapt to the new idea of never typing, changing, or even knowing a password. Moreover, these initial users can help educate other users as you implement it across the organization.
Also Read: Managed Detection and Response (MDR): Overview and Importance
Final Thoughts
Passwordless authentication is finally seeing real traction in the IT world. However, it’s still evolving. Understand that you are shifting from a widely adopted security method – passwords – to a younger but modern one. Moving beyond passwords demands major IT upgrades as well as changes to other business processes. You may also experience employee inertia as they may assume that this new approach will be daunting and complex.
These challenges should not bog you down from going passwordless. Security leaders like StealthLabs can help you evolve to the next level of authentication. Our security experts shall assist you in fixing fundamental facets before embarking on the password-free journey. Reach out to us today to get started with passwordless authentication.
More Articles:

