Over 80% of businesses rely on mobile applications for their daily operations and real-time communication.
From web conferencing to banking, a lot is being done through mobile phone applications. Though mobile apps are convenient and user-friendly, they are often insecure and may expose you and your organization to security risks.
So, one must confirm whether the application has passed the necessary security checks and is secure.
Studies indicate that over 76% of mobile applications have poor data storage, indicating a severe threat to your login credentials, personal and financial data.
However, many users are not aware of this because mobile applications, unlike websites or web applications, come with a different set of security challenges that can only be determined through ‘Penetration testing’, also called ‘pen test’, ‘pentest’, or ‘ethical hacking’.
Here is a roadmap that lets you pen test mobile applications in an organized manner.
Penetration Testing: Approach, Process, and Tools
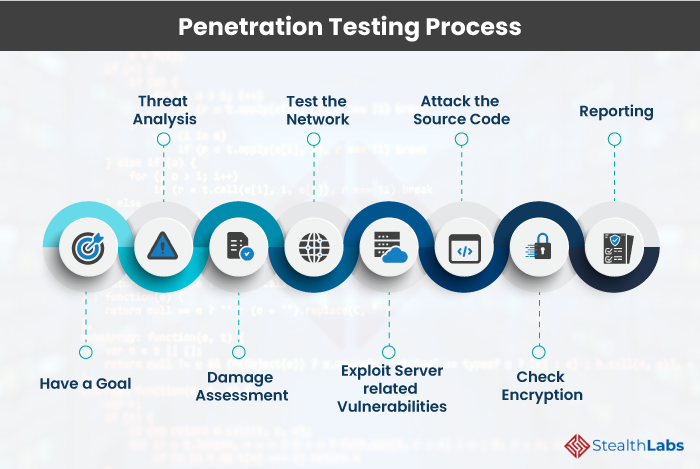
1) Have a Goal
You need to know what constitutes a mobile application before pen testing it. You need to test three constituents — the application, the API, and the server that hosts the API. Then again, you need to test the network communication and permission-related inconsistencies.
So, confirm whether the application seeks excessive permissions that can be used for malicious purposes. Other potential flaws include source code issues, erratic security configurations, in-app configuration errors, and insecure data storage. So, you need to figure out which areas you wish to pen test and then proceed further.
2) Threat Analysis
Now that you have laid the foundation for penetration testing by identifying common issues, it is time to plan a more comprehensive threat analysis.
This involves reviewing application architecture, checking app resources, analyzing third-party interaction, etc. For this, you must finalize a platform-specific or all-platform compatible testing software.
In the case of Android apps, you may choose packages like Appie or Android Tamer.
On the other hand, if you wish to pick something that works with Android and iOS applications, try the MobSF or Needle. Again, if you want to perform both static and dynamic analysis for Android and iOS apps, we recommend the MobSF application only.
It is a rare threat analysis tool supporting both APK and IPA binaries and the zipped source code. Another great tool is the Quick Android Review Kit (QARK) by LinkedIn, which is improvised continuously.
3) Damage Assessment
Now that you have a fair idea about the mobile application’s vulnerabilities, it becomes easier to gauge how bad it can get. It is imperative to prioritize vulnerabilities that can result in something like a handset overtake or phishing.
A handset overtake is the most critical type of attack that provides the threat actor with complete access to the mobile device’s data. Phishing, however, involves inducing users to reveal their sensitive information under false pretexts. Other forms of cyberattacks include Cryptojacking (also called malicious Cryptomining), man-in-the-middle attacks, and Malvertising.
4) Test the Network
In the world of mobile app security, network attacks are the most widespread threat and must therefore be thoroughly investigated. They occur when the data is in transit between the client and the server because this is when jitters and packet loss occur.
You can dig into these issues using the Zed Attack Proxy (ZAP), yet another open-source penetration testing tool. In doing so, ensure that the authentication occurs via the SSL Certificate and not the HTTP, which can be easily intercepted.
5) Exploit Server-related Vulnerabilities!
The server which hosts the mobile application may contain potential vulnerabilities, which the pen tester must attempt to exploit.
Unless these are identified and fixed, the server-client communication may be leaked or exposed. You can locate such exploits by using network mapping tools such as Nmap, Angry IP Scanner, SolarWinds Port Scanner, Wireless Network Watcher, etc.
These tools allow you to detect other devices using the same network, open ports, and more. So, you can attempt to mimic attacks such as man-in-the-middle, packet sniffing, etc.
6) Attack the Source Code
Attackers often manipulate the mobile application’s source code to gain unauthorized access to the device or steal data. The most common threat is SQL injection, which involves inserting malware in the form of data input, which is then executed and processed like other data. However, unlike other normal data, this malicious data injected by the threat actor transforms into executables.
Therefore, a pen tester must unpack the application package and confirm that no changes have been made to the binary configurations.
Another way to find issues with the source code is through reverse engineering, which involves decompiling the code from machine language to human-readable. It can then be examined for potential threats.
7) Check Encryption
Most mobile applications either make use of an outdated encryption algorithm or install a secure one incorrectly. In either case, the result is the same — weak encryption, which works to the threat actor’s advantage.
You need to ensure that the mobile application is not using ineffective and inefficient algorithms like the MD4, MD5, SHA-1, BLOWFISH, DES, 3DES, RC2, and RC4. None of these keep the client-server exchange safe, so use something reliable like the 256-bit Advanced Encryption Standard (AES) or SHA-2 algorithms. Also, ensure that those are correctly configured and installed.
8) Reporting
Now that you have launched attacks and identified vulnerabilities, it is time to document them properly. This must provide a complete summary of the discovery process, environment creation tools, exploits manipulated, and your findings.
Finally, recommend remediation measures that can strengthen the security of the mobile application. Do not go too deep into the technicalities because this report usually goes to the top management.
Final Takeaway
Mobile applications hosted on even the most popular libraries such as Playstore may turn out to be insecure. It does not necessarily apply to gaming and entertainment applications only. Almost any app, including banking, finance, and eCommerce mobile applications, may contain vulnerabilities that mobile phone users must watch out for.
Those in charge of an organization’s IT administration must test mobile applications before their employees use them for professional purposes.
The best way to do so is by penetration testing the application through the pen-testing tools mentioned above.
More Articles:

