Microsoft Exchange Hack: Attackers Send Spams to Existing Email Chains!
The Microsoft Exchange Hack harnessed a new range of cyber tactics to distribute malware and bypass detection.
Researchers at Trend Micro have recently discovered that perpetrators were tactically sending malicious emails as replies to preexisting email chains. As a result, this tactic potentially lowers a victim’s guard against malicious activities, paving the way for hackers to perpetuate their attacks.
Microsoft Exchange Hack Explained
To pull this off, hackers are exploiting ProxyLogon (CVE-2021-26855) and ProxyShell (CVE-2021-34473 and CVE-2021-34523) vulnerabilities found in Microsoft Exchange Server.
The ProxyLogon vulnerability enables a malicious actor to send a specially crafted web request to an Exchange Servicer. The request bypasses authentication, allowing the attacker to execute EWS requests encoded in the XML payload and ultimately perform operations on victims’ mailboxes.
Also Read: Robinhood Suffers Yet Another Massive Breach!
With this bypass, the hackers can purportedly obtain users’ SIDs and emails. Moreover, they can even search for and download a particular user’s emails. After obtaining illegitimate access to the email threads, the hackers can deliver their malicious spam as replies to the said threads.
These emails originate from an internal network on an on-premises Exchange Server and appear to be a continuation of the email threads. Therefore, the user instinctively believes that the email is legitimate and secure.
This tactic is not only effective in distributing malware, but it is also excellent in bypassing screening at the email security systems.
How did It happen?
Trend Micro claimed that the threat actor ‘TR’ is behind this tactical attack. The attacker distributed emails with malicious attachments, for instance, IcedID, Qbot, Cobalt Strike, and SquirrelWaffle payloads.
Also Read: Kaseya Ransomware Attack
For example, the attacker sent spam as replies to existing email threads to all the internal users as below:
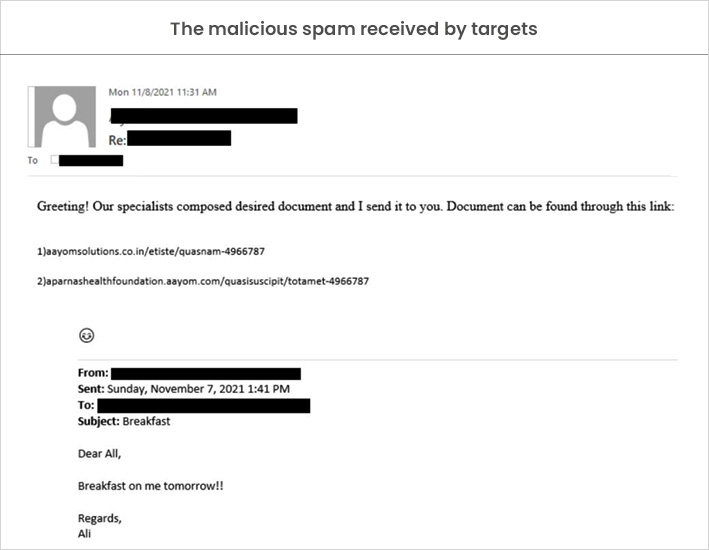
“In the intrusion, we analyzed email headers for malicious emails received, the mail path was internal (between mailboxes of three internal Exchange servers), indicating that the emails did not originate from an external sender, open mail relay, or .Any Message Transfer Agent (MTA),” said Trend Micro.
Moreover, the hacker used actual account names from the victim’s domain as sender and recipient. As a result, this potentially increased the possibility of a recipient accessing the link and opening the malicious mail attachment.
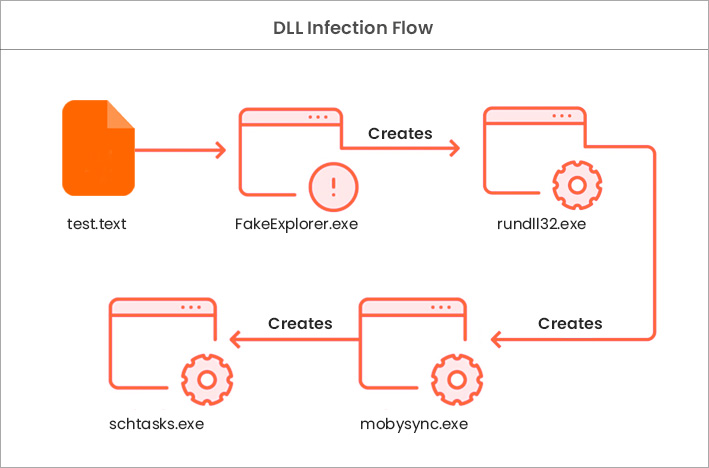
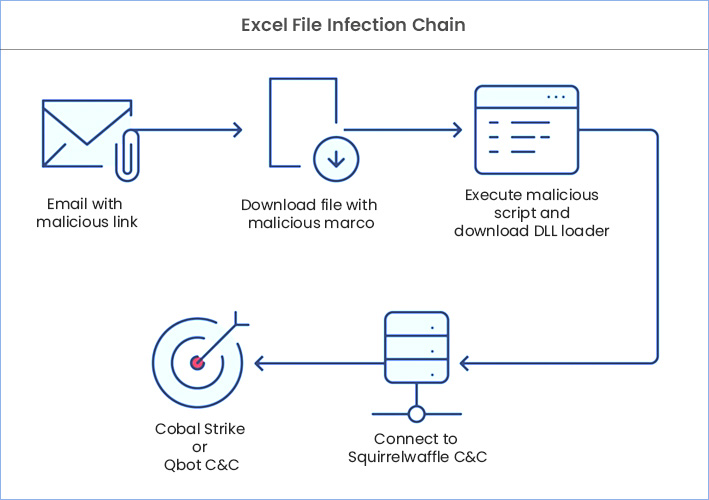
According to the tech firm, links used in the malicious emails dropped a ZIP file in the victim’s system. The ZIP file contained a malevolent Microsoft Excel sheet that downloads and executes a malicious DLL related to Qbot.
The sheets were ingrained with malicious Excel 4.0 macros for downloading and executing the malicious DLL.
“Delivering the malicious spam using this technique to reach all the internal domain users will decrease the possibility of detecting or stopping the attack, as the mail getaways will not be able to filter or quarantine any of these internal emails,” claimed Trend Micro.
“The attacker also did not drop or use tools for lateral movement after gaining access to the vulnerable Exchange servers, so that no suspicious network activities will be detected. Additionally, no malware was executed on the Exchange servers that will trigger any alerts before the malicious email is spread across the environment.”
How can one prevent these malicious emails?
The Microsoft Exchange Server hack underscores the tactics attackers use to mask malicious emails and files. One must take heed of the unearthed fact that emails originating from trusted contacts or networks may not indicate that the contents of the email are trustworthy and secure.
Here are some security recommendations to consider:
- Ensure to patch Exchange Server vulnerabilities, specifically ProxyShell and ProxyLogon
- Deploy virtual patching modules on all Exchange Servers that have not yet been patched for the mentioned vulnerabilities
- Leverage Endpoint Detection and Response (EDR) solutions to gain higher visibility into the internal network and identify any suspicious behavior on servers
One can also seek the assistance of Managed Detection and Response (MDR) service providers like StealthLabs to protect the systems.
We utilize advanced threat intelligence to correlate and prioritize threats and identify if they are part of a larger attack. Let’s collaborate to make your business cyber-safe.
More News:
- DeFi Firm Cream Finance Suffers Crypto Hack, Loses USD 130 Million!
- Robinhood’s Hack Worsens: Threat Actor Pilfers 4,400 Phone Numbers!
- 95% of Ransomware Attacks Target Windows Devices: Google’s VirusTotal
- Microsoft Blames Russia for Most Cyberattacks
- Cybercriminals Leveraging Telegram Bots to Bypass MFA and OTP
- Microsoft Suffers Yet Another Breach!
- REvil’s Faux Pas Thwarts Massive Ransomware Attack