In recent years, ransomware has become the most rampant form of cybercrime. Organizations, irrespective of their business sizes and nature, are becoming victims of ransomware attacks now.
The latest stories, including Kaseya, JBS, and Colonial Pipeline ransomware attacks, are proving that they can have an overwhelming impact on businesses of all sizes.
Ransomware threats can impede businesses, deter productivity, and potentially set an entire organization up for failure. And, in many cases, victims end up paying huge ransoms to regain access to their systems. According to a recent 2021 State of Ransomware survey, 83 percent of companies that experienced a ransomware attack in the last 12 months coughed up the ransom.
Also Read: REvil’s Faux Pas Thwarts Massive Ransomware Attack
One prime reason organizations fall victim to this devastating threat is the lack of awareness about ransomware trends and response methods.
Here are some key findings from VirusTotal’s Ransomware Activity Report to help you understand the nature of ransomware attacks, how they develop, and how they might evolve in the future:
Commissioned by Google, VirusTotal analyzed more than 80 million potential ransomware-related samples submitted by users from over 140 countries since 2020.
Also Read: Accenture Suffers Ransomware Attack
The report, titled Ransomware in a Global Context, facilitates comprehensive visibility into how ransomware attacks spread and evolve. Let’s delve into the details:
Key Findings on Ransomware Report in 2020 and 2021:
-
Most affected countries by ransomware
The comprehensive analysis of 80 million ransomware samples from 140 countries revealed that Israel is the most affected territory, with an almost 600% rise in the number of submissions compared to its baseline.
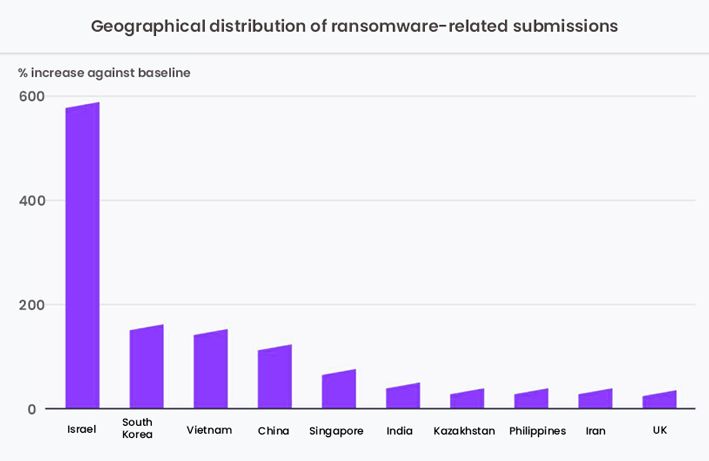
The other nations in the Top 10 affected territories are South Korea, Vietnam, China, Singapore, India, Kazakhstan, the Philippines, Iran, and the UK.
-
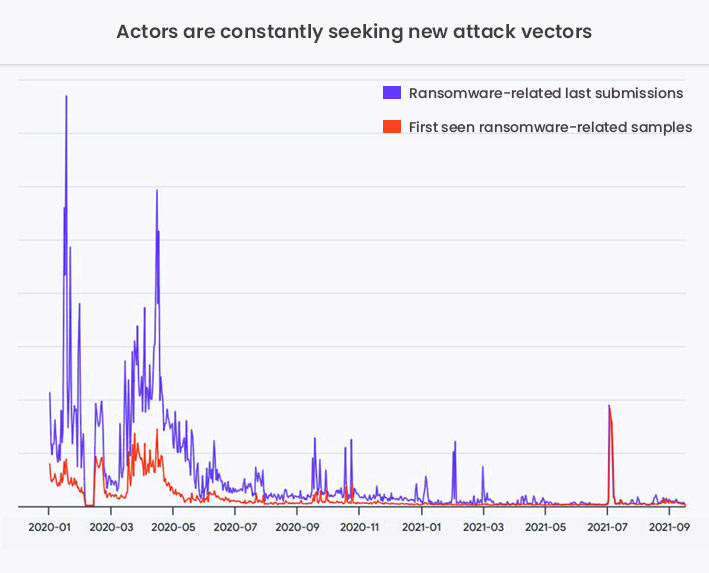
Actors are constantly seeking new attack vectors
In the survey, VirusTotal found that cybercriminals are constantly molding their attack tactics and exploiting new attack vectors. “It seems that in most cases attackers prepare fresh new samples for their campaigns,” said the security firm in the report.
-
130 ransomware families have been active since 2020
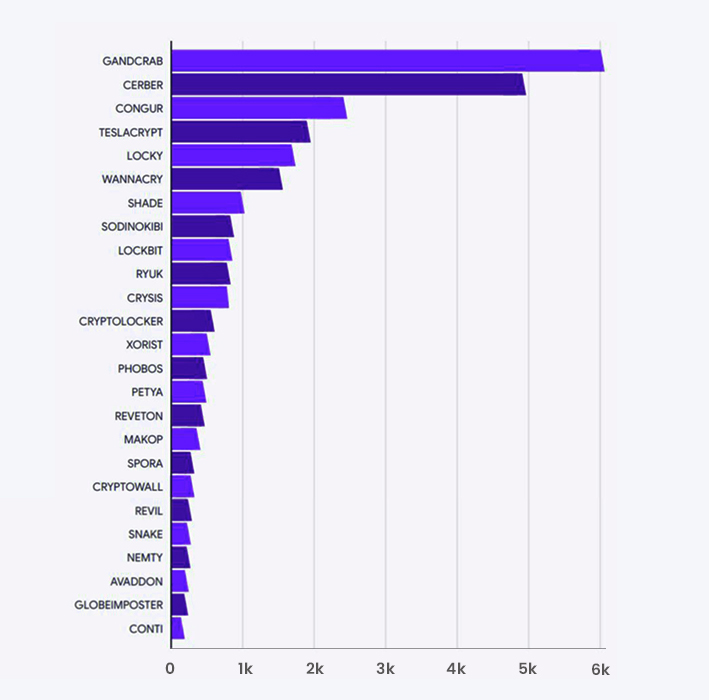
VirusTotal identified that at least 130 different ransomware families were active since 2020. GandCrab is the most active ransomware family during the survey period, accounting for 78.5% of the samples.
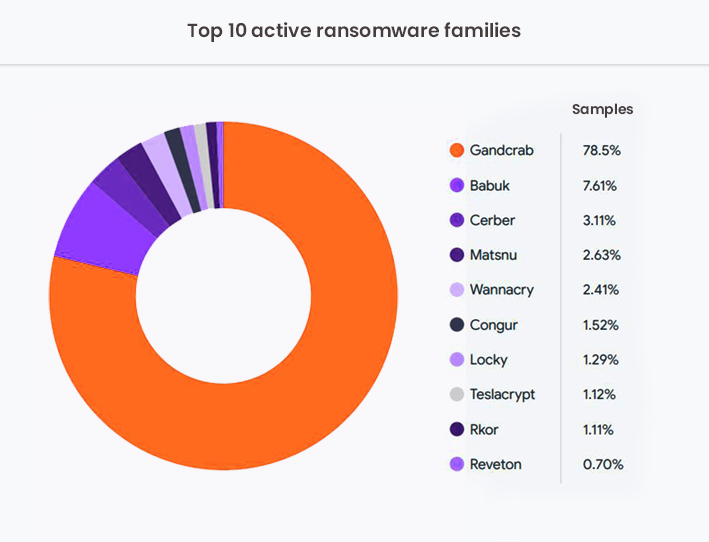
“GandCrab had an extraordinary peak in Q1 2020, which dramatically decreased afterwards. It is still active but at a different order of magnitude in terms of the number of fresh samples,” reported VirstuTotal.
Accounting for a significant portion of samples, the GandCrab ransomware gang made the rest of the families almost negligible. The second most active ransomware family Babuk accounted for a mere 7.61% of samples. It is followed by Cerber (3.11%), Matsnu (2.63%), and Wannacry (2.41%).
-
Almost 94% of ransomware files were Windows-based executables
The study identified that 95% of the scanned ransomware files were Windows-based executables (93.28%) or dynamic link libraries (2%). Meanwhile, Android accounted for 2.09% of the ransomware targets.
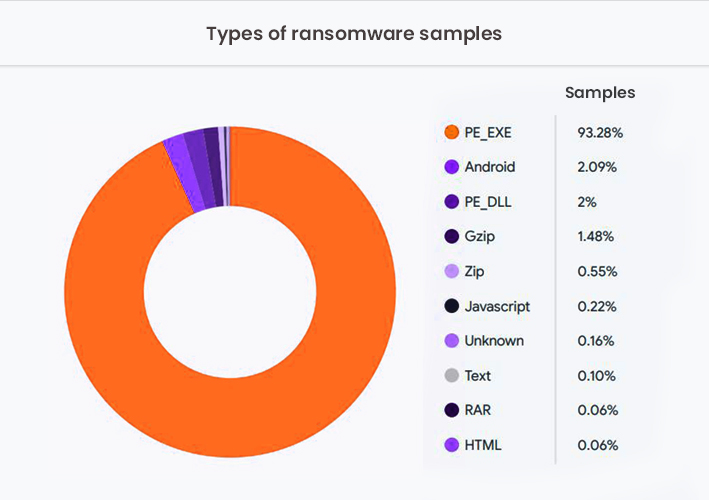
Perhaps surprisingly, the survey found that only 5% of the scanned samples were relating to exploits, “most commonly Windows elevation of privileges and SMB information disclosures and remote execution.” This reveals that malicious actors don’t need exploits for conducting ransomware attacks. Instead, they appear to need exploits only for privilege escalation and malware spreading within internal networks.
-
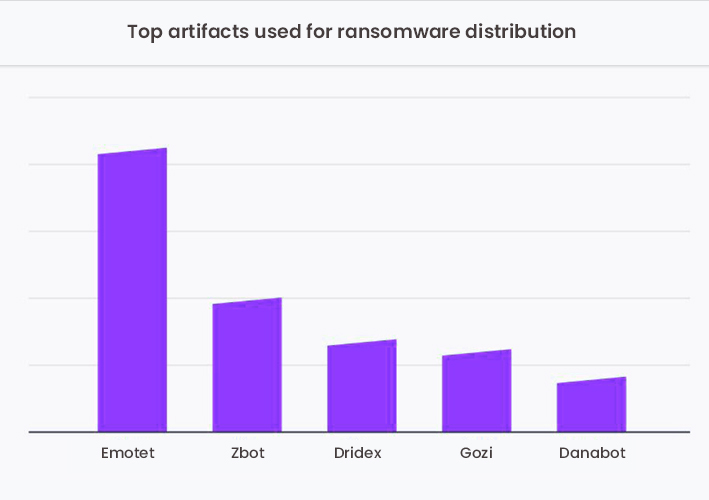
Top artifacts used for ransomware attacks
Malicious actors are using a wide range of artifacts for ransomware distribution and lateral movement. Among the various distribution artifacts used by cybercriminals to spread ransomware, Emotet took the lion’s share of the blame. It is followed by Zbot, Dridex, Gozi, and Danabot.
“Attackers are using a range of approaches, including well-known botnet malware and other Remote Access Trojans (RATs) as vehicles to deliver their ransomware,”
“In terms of artifacts used for other stages of the attack such as lateral movement, we identified the use of Mimikatz and Cobaltstrike, several scripting languages such as AutoIT and Powershell, and dozens of remote access Trojans (RATs) such as Phorpiex, Smokeloader, Nanocore, and Ponystealer,” said the report.
Are you resilient in face of ransomware threats? StealthLabs can help!
More News:

