Ransomware attacks are on the rise in recent years, both within the US and globally.
These attacks continue to capture headlines, heightening public awareness and mounting concerns about how to avoid them.
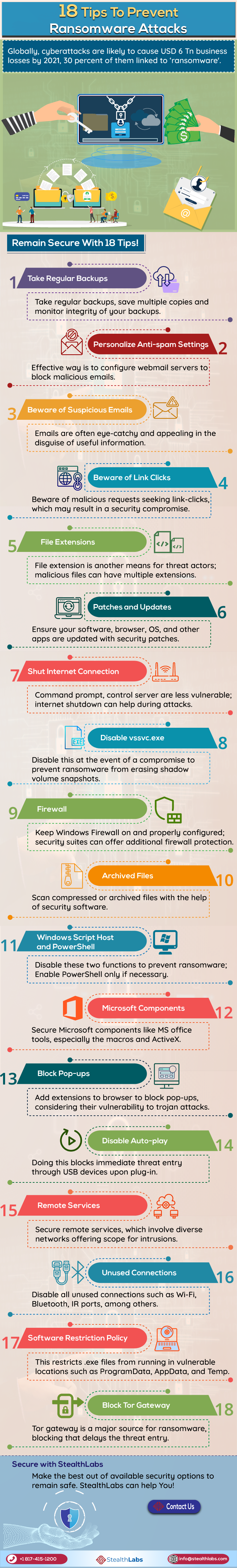
Globally, cyberattacks are likely to cause USD 6 trillion in the business loss by 2021 and 30% of them are linked to ‘Ransomware‘.
So, securing digital entities from ransomware is crucial to ensure business continuity.
Here is an infographic with 18 tips to prevent ransomware attacks:
ALSO READ | 6 Ways to Avoid Falling Victim to Phishing Scams
How To Prevent Ransomware Attacks:
1) Take Regular Backups: Take regular backups, save multiple copies, and monitor the integrity of your backups.
2) Personalize Anti-spam Settings: An effective way is to configure webmail servers to block malicious emails.
3) Beware of Suspicious Emails: Emails are often eye-catchy and appealing in the disguise of useful information.
4) Beware of Link Clicks: Beware of malicious requests seeking link clicks, which may result in a security compromise.
5) File Extensions: File extension is another means for threat actors; malicious files can have multiple extensions.
6) Patches and Updates: Ensure your software, browser, OS, and other apps are updated with security patches.
7) Shut Internet Connection: Command prompt, and control servers are less vulnerable; an internet shutdown can help during attacks.
8) Disable vssvc.exe: Disable this in the event of a compromise to prevent ransomware from erasing shadow volume snapshots.
9) Firewall: Keep Windows Firewall on and properly configured; security suites can offer additional firewall protection.
10) Archived Files: Scan compressed or archived files with the help of security software.
11) Windows Script Host and PowerShell: Disable these two functions to prevent ransomware; Enable PowerShell only if necessary.
12) Microsoft Components: Secure Microsoft components like MS office tools, especially the macros and ActiveX.
13) Block Pop-ups: Add extensions to browsers to block pop-ups, considering their vulnerability to trojan attacks.
14) Disable Auto-play: Doing this blocks immediate threat entry through USB devices upon plug-in.
15) Remote Services: Secure remote services, which involve diverse networks offering scope for intrusions.
16) Unused Connections: Disable all unused connections such as Wi-Fi, Bluetooth, and IR ports, among others.
17) Software Restriction Policy: This restricts .exe files from running in vulnerable locations such as ProgramData, AppData, and Temp.
18) Block Tor Gateway: Tor gateway is a major source for ransomware, blocking that delays the threat entry.
Secure with StealthLabs
Make the best out of available security options to remain safe. StealthLabs can help you!
More Stories:

