There’s no stopping cybercrime.
The recent cyber incidents, including the T-Mobile hack and Fortinet data breach, depict how cybercriminals are inflicting severe damage on enterprises across all industry segments. Executing cyberattacks has become a cakewalk, as threat actors are constantly adopting more profitable, effective, and efficient tactics.
As they face robust defenses to their attack vectors, cybercriminals are switching to trying out new tactics, techniques, and procedures (TTPs). And, according to a recent report from cybercrime intelligence firm Intel 471, the latest development in cybercrime tactics and scams involves the use of robocalls and Telegram bot.
As per the report, cybercriminals are leveraging robocalling and Telegram bots to bypass Multi-Factor Authentication (MFA) in scams. Ironically, MFA is considered the most effective security strategy to prevent account takeovers.
The MFA bypassing involves using robocalls with interactive messages that deceive users into sharing their one-time passwords (OTPs).
Also Read: T-Mobile Hack Exposes Personal Data of 47 Million Customers!
Telegram-based bots have been misused by the cybercriminals into automating and controlling these bypassing processes. It is relatively as simple as organizations using Slack bots to automate work routines.
“Intel 471 has seen an uptick in services on the cybercrime underground that allow attackers to intercept one-time password (OTP) tokens.
We’ve seen actors provide access to services that call victims, appear as a legitimate call from a specific bank and deceive victims into typing an OTP or other verification code into a mobile phone to capture and deliver the codes to the operator,” said the company.
“Some services also target other popular social media platforms or financial services, providing email phishing and SIM swapping capabilities.”
Automating Social Engineering Attacks Using Bots
At their core, these MFA bypass attacks are highly automated social engineering attacks. In the past, the malicious actors manually called a victim to elicit PII or service provider to gain unauthorized access to an account. However, attackers are now performing scripted calls using bots that rely on commands given in a Telegram chat.
“All the services Intel 471 has observed, which have only been in operation since June, either operate via a Telegram bot or provide support for customers via a Telegram channel,” said the researchers.
“In these support channels, users often share their success while using the bot, often walking away with thousands of dollars from victim accounts.”
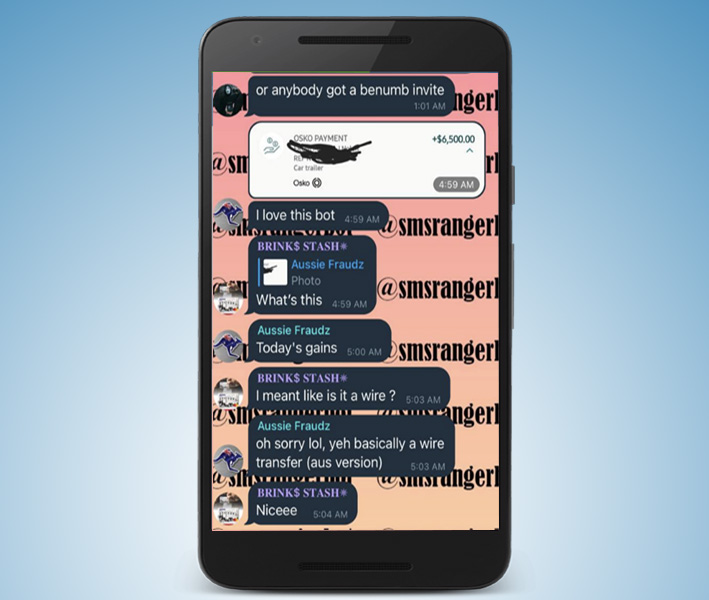
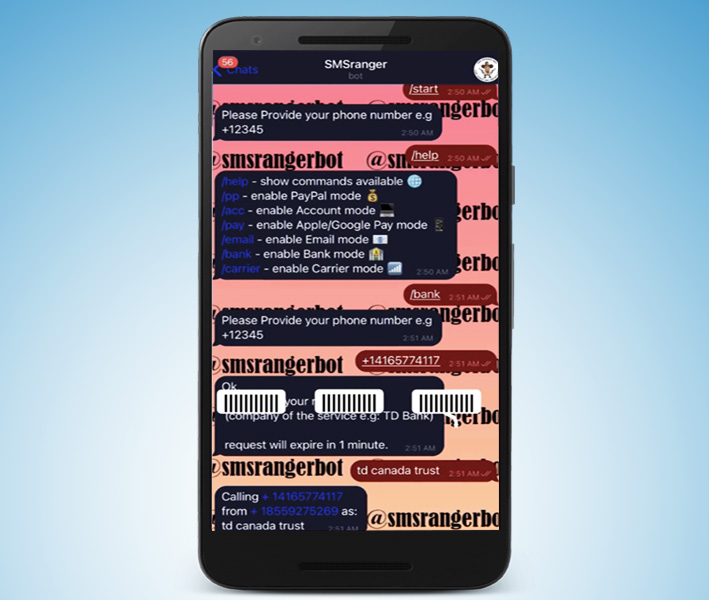
Intel 471 found one particular bot called SMSRanger that is extremely easy to use. A simple slash command enables users to impersonate various banks and online payment services like PayPal, Apple Pay, Google Pay.
Also Read: IT Company Discovers New, Startling Vulnerabilities in Azure
Once the malicious actor provides the victim’s phone number, the bot automatically handles the remaining work, ultimately granting access to the victim’s account. SMSRanger claims to have a success rate of 80% if the victim answers the call and the attacker provides accurate information about the victim.
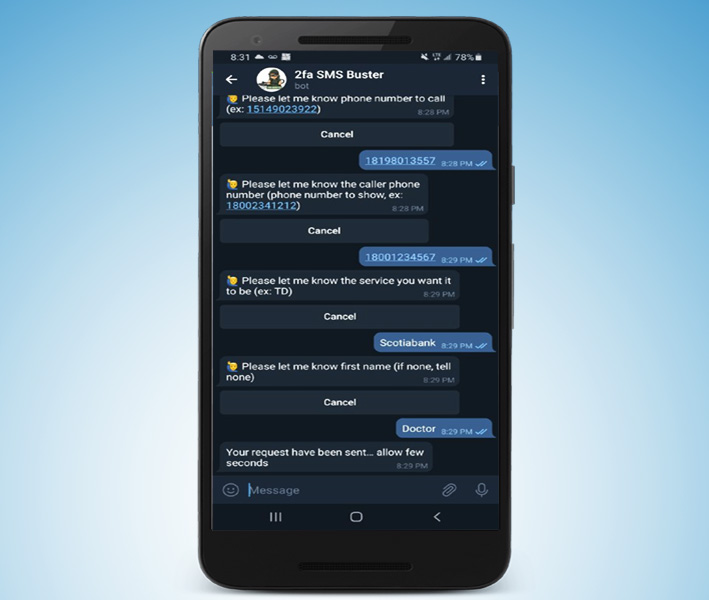
Another bot named SMSBuster offers options to disguise a call as a legitimate contact from a specific bank. From there, the bot follows a script to deceive victims into providing sensitive information such as ATM PIN, CVV, and OTP. Then, the bot would send the details to the attacker’s Telegram account.
Also Read: LockBit Hackers Exploit Accenture to Compromises an Airliner!
According to Intel 471, SMSBuster has been used to illegally access accounts at eight different Canada-based banks.
A Cakewalk
Launching an attack has become effortless for malicious actors with Telegram-powered bots. Though creating bots need programming ability, a user just needs some money to access the bot. A monthly fee of USD 300 is all required to obtain the authentication code needed for operating the bot.
Also Read: REvil’s Faux Pas Thwarts Massive Ransomware Attack
Another USD 20-100 more can provide access to live phishing panels that target accounts on social media platforms like Facebook, Snapchat, Instagram, financial apps like PayPal, Venmo, Robinhood, and cryptocurrency marketplace Coinbase.
Time to Adopt!
The Telegram bot scams reveal that multi-factor authentication has its own security flaws. SMS- and phone call-based OTP options have now become feeble
It’s time for organizations to adopt more robust forms of MFA, including Time-Based One Time Password (TOTP) codes, push-notification-based codes, or a FIDO security key. After all, prevention is always better than the cure.
More News:
- Microsoft Suffers Yet Another Breach!
- User Misconfigurations in Microsoft Power Apps Exposes 38 Million Records!
- World’s Largest Meat Company Ends Up Losing USD 11Mn Due to Ransom Attack!
- AT&T Purportedly Breached! 70 Million Users’ Data Compromised
- Accenture Suffers Ransomware Attack; USD 50 Million Ransom Demanded
- Security Firm Fortinet Suffers Cyberattack, Almost 500,000 VPN Account Credentials Leaked
- Kaseya Ransomware Attack: Hackers Demand USD 70 Million in One of the Largest Cyberattacks!

