It appears that there’s no stopping cybercrime. Malicious actors are burning the candle at both ends to gain global notoriety. T-Mobile data breach is their latest work of art.
In the most recent T-Mobile hack, hackers gained access to the personal data of more than 47 million customers. The brazen data heist could empower criminals with the digital keys to conduct widespread online fraud.
“We have determined that unauthorized access to some T-Mobile data occurred,” confirmed T-Mobile days after a subset of stolen customer data was listed for sale on a hacker’s forum.
“Late last week, we were informed of claims made in an online forum that a bad actor had compromised T-Mobile systems. We immediately began an exhaustive investigation into these claims and brought in world-leading cybersecurity experts to help with our assessment,” the company informed.
The American telecom giant said the hackers stole the personal information of over 40 million former or prospective T-Mobile customers and the data of approximately 7.8 million current customers.
The exposed data includes first and last names, birth dates, social security numbers, and driver’s licenses, said the network carrier. It also comprised account PINs of around 850,000 active prepaid customers. Fortunately, the stolen data didn’t contain any financial information.
Also Read: Colonial Pipeline Ransomware Attack
“We have no indication that the data contained in the stolen files included any customer financial information, credit card information, debit or other payment information,” stated the cellular carrier.
100 Million Customers’ Records?
While T-Mobile stated that data of over 47 million customers was exposed, a seller on a known hacker’s forum told Motherboard they possess data of 100 million T-Mobile customers.
“T-Mobile USA. Full customer info,” the seller told Motherboard.
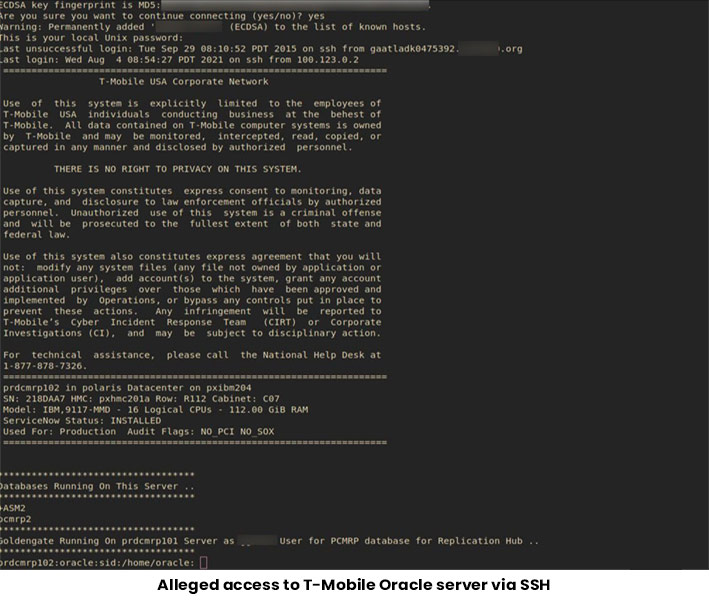
The malicious actor claimed they had compromised T-Mobile’s production, staging, and development servers. It also compromised an Oracle database server, containing customer data two weeks ago.
Also Read: JBS Ransomware Attack
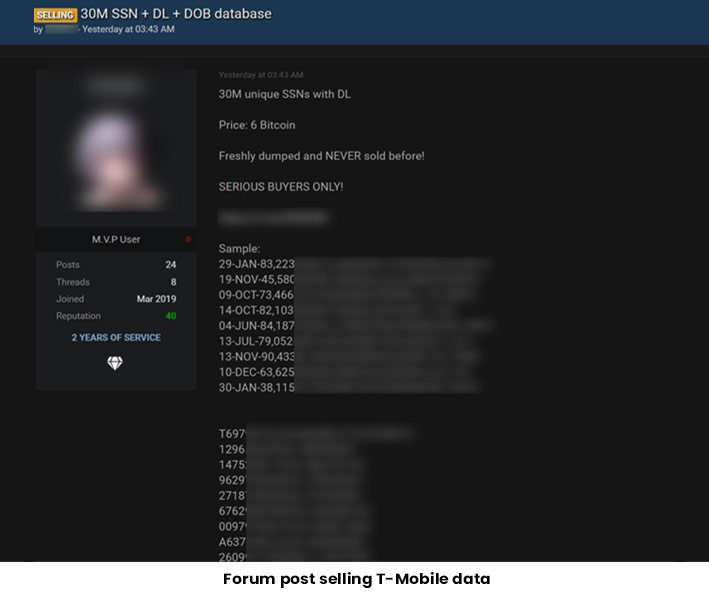
On the forum, the hacker is selling 30 million SSNs and driver licenses for six bitcoins ($280,000). The seller informed Motherboard that they are selling the rest of the data privately.
Cyber experts claim that the stolen data could be vehicles to commit fraud such as identity theft and SIM swapping. The latter is a notorious attack in which cybercriminals seize control of a victim’s mobile phone.
“It’s probably the biggest gift to SIM-swappers they’ve received in years,’ opined Allison Nixon, chief research officer at cyber services company Unit 221B.
“The typical life cycle of these databases is first they start in the hands of the very few, but it will spread because people share data. All of these hacked databases eventually go public,” she said.
A Prompt Response!
T-Mobile proactively closed the entry points used by the threat actors to gain access to the giant’s servers.
“We are confident that the entry point used to gain access has been closed, and we are continuing our deep technical review of the situation across our systems to identify the nature of any data that was illegally accessed,” announced T-Mobile.
“We immediately began an exhaustive investigation into the data breach claims and brought in world-leading cybersecurity experts to help with our assessment.”
Also Read: Kaseya Ransomware Attack
“We then located and immediately closed the access point that we believe was used to illegally gain entry to our servers,” reassured the telecom giant.
The hacker’s announcement corroborates the company’s declaration, saying “I think they [T-Mobile] already found out because we lost access to the backdoored servers.”
The company also proactively reset all the PINs of the 850,000 active prepaid customer accounts. It also recommended postpaid customers change their PINs.
“Recommending all T-Mobile postpaid customers proactively change their PIN by going online into their T-Mobile account or calling our Customer Care team by dialing 611 on your phone,” said the company in a statement.
The company also offered its customers two years of free identity protection services with McAfee’s ID Theft Protection Service.
US Telecoms Agency Arrives on the Scene

The US Federal Communications Commission (FCC) announced that it would investigate the T-Mobile hack.
“Telecommunications companies have a duty to protect their customers’ information. The FCC is aware of reports of a data breach affecting T-Mobile customers, and we are investigating,” said an FCC spokesperson.
With this latest data breach, it is the fifth T-Mobile hack in recent years.
In Jan 2021, T-Mobile suffered a hack that exposed about 200,000 call records and other subscriber data.
The telecom company witnessed two incidents in 2020. In the first attack, cybercriminals hacked the giant’s email systems and accessed employee email accounts and customer data. Whereas in the second breach, the personal and billion information of a million prepaid customers were public.
In 2018, T-Mobile announced that hackers stole as many as two million customers’ personal information.
More News Article:
- Accenture Suffers Ransomware Attack; USD 50 Million Ransom Demanded
- Future of Cybersecurity: 5 Trends That Need Close Monitor!
- 6 Ways To Avoid and Remain Safe From ‘Phishing Attacks’
- Autonomous Car Security: Adversarial Attacks Against New Mobility!
- Cybersecurity in Education: 10 Important Facts and Statistics
- Cyber Security Services for Education & Research Institutions

