86% of Compromised Google Cloud Accounts Leveraged for Crypto Mining!
Cloud has become a business imperative amid the pandemic. It has enticed businesses with a host of benefits, including flexibility, agility, scalability, and innovation. However, in reality, many companies are lagging behind in their uptake of cloud tech. Concerns over Google cloud security is the prime factor impeding their cloud adoption.
The 2021 Cloud Threat Intelligence Report by Google Cloud revealed that cloud customers continue to face various cyber threats, including cryptocurrency mining abuse, phishing campaigns, and ransomware.
According to the threat intelligence observations, malicious hackers are exploiting inadequately secured cloud instances to download cryptocurrency mining software to the compromised system.
“Of 50 recently compromised GCP instances, 86% of the compromised Cloud instances were used to perform cryptocurrency mining, a Cloud resource-intensive, for-profit activity,” reported Google.
In addition, 10% of the compromised instances were used for identifying vulnerable systems by conducting port scanning of other publicly available resources on the internet. Meanwhile, 8% of the instances were exploited for launching attacks against other targets on the internet.
Also Read: Panasonic Suffers Data Breach; Remains Undetected for Ages
Surprisingly, data theft was not the prime objective of these compromises, said Google Cloud. Instead, the malicious actors focused on the cloud asset compromises to perform multiple forms of abuse.
The public internet-facing Cloud instances were used for scanning and brute force attacks, mentioned Google.
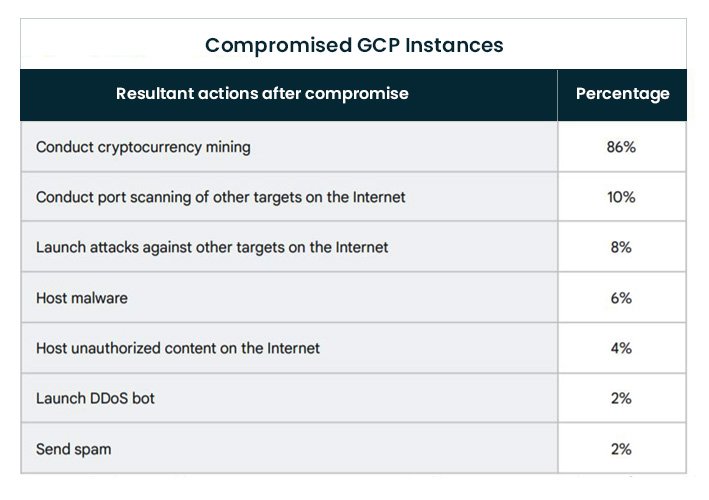
The other key findings is that weak or no password is the prime attack vector exploited by cybercriminals to comprise Google Cloud accounts.
According to the report, “48% of compromised instances were attributed to actors gaining access to the internet-facing Cloud instance, which had either no password or a weak password for user accounts or API connections.”
Additionally, 26% of cloud compromises were due to vulnerabilities in third-party software.
Moreover, Google revealed that time is crucial in cloud breaches.
“Time was of the essence in the compromise of the Google Cloud instances. The shortest amount of time between deploying a vulnerable Cloud instance exposed to the internet and its compromise was determined to be as little as 30 minutes,” reported GCP.
The report revealed that the time to compromise was below eight hours in 40% of Cloud instances.
Also Read: Microsoft’s Bug Exploited by Threat Actor; Multiple Users Compromised!
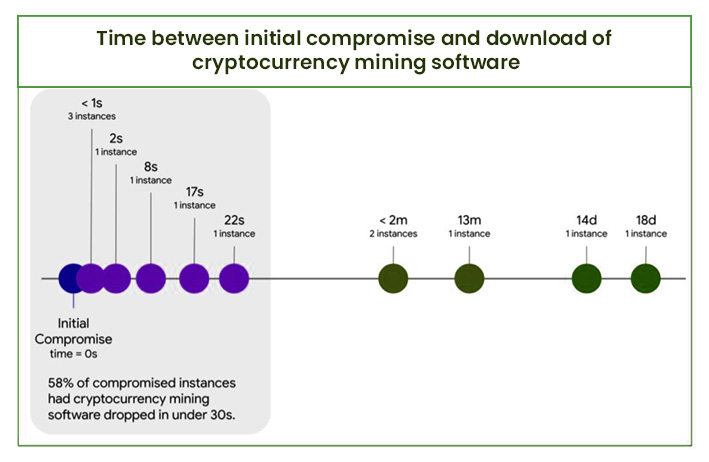
By analyzing the systems leveraged for performing cryptocurrency mining, the GCP reported that in 58% of compromised cloud instances, the crypto mining software was downloaded to the system within 22 seconds after compromise.
The short time indicates that the initial attacks and subsequent downloads were automated events, without any need for human intervention.
“The ability to manually intervene in these situations to prevent exploitation is nearly impossible. The best defense would be not to deploy a vulnerable system or have automated response mechanisms,” said GCP.
This report underscores the need for inculcating good cyber hygiene across the organization. Enterprises must ensure that cloud accounts always have strong passwords. In addition, one ought to engage employees in email best practices, implement multiple-factor verification, and authenticate downloads with hashing and verifying.
However, managing resources on the cloud alongside implementing these google cloud security best practices can be tough. One must take heed of the fact that sailing on two boats could potentially push you into the hot water. This is where the services of StealthLabs come in handy.
StealthLabs has a decade-long experience in catering to the security needs of SMBs and Fortune 500 companies. Our elite team of cloud security experts helps swiftly identify security gaps and establish a proactive-based baseline cloud security.
We can empower you to automate the deployment of security guardrails for cloud platforms, including AWS, Microsoft Azure, and Google Cloud. Let’s collaborate to secure your cloud from evolving threats and complex regulatory requirements.
More News:

