Cybersecurity Incident Response Services
In today’s digital ecosystem, no business is immune from a potential cyberattack.
Cyberthreats are evolving rapidly, increasing in frequency, complexity, and intensity. Hacked systems, breached networks, crashed websites, denial of service, stolen credentials, and other cyber incidents have become common.
It’s no longer a question of if your organization will experience an attack. It’s a question of when.
This is where Cyber Incidence Response (CIR) comes to the fore! To quickly mitigate the damage and enable business continuity. However, developing and maintaining in-house CIR capability can be time-consuming, resource-intensive, and complicated. That’s where StealthLabs can help.
StealthLabs’ Cyber Incident Response Services and Solutions help your organization develop processes and strategies to respond quickly during an incident. Our industry-specific experience and technology assets enable you to be confident that you have the capability and support to deal with any incident effectively and efficiently.
The Benefits of Incidence Response
A robust cyber incidence response capability has become a business imperative for organizations that seek to build a secure, vigilant, and resilient landscape. A reliable CIR plan can help your organization:
- Quickly understand the nature of an incident – To help address and answer the questions regarding the attack
- Reduce the costs associated with a data breach – In terms of the cost of time, resources, and brand reputation
- Introduce robust management and controls – To strengthen your IT and business processes, enabling focus on core activities that deliver value for the organization.

How to Develop a Successful Incidence Response Plan?
Developing an IR plan involves a 6-step framework as follows:
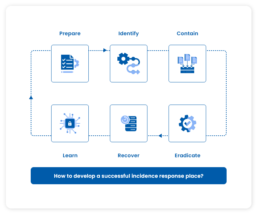
-
Prepare
Define an organization-level security policy, what qualifies as a security incident, and a step-by-step guide on how to handle an incident. -
Identify
Define what criteria, specific kind of security issue, or a cumulative set of circumstances trigger the IR plan. -
Contain
Stop the threat from spreading and doing further damage by implementing short-term or long-term containment processes. -
Eradicate
Establish a process to restore all the compromised systems and update the defense system to prevent the same security incident from occurring again. -
Recover
Determine a strategy to bring all systems back into full production. -
Learn
Review the documentation of the incident and update the IR plan based on the feedback.
How StealtLabs Help Organizations With Incident Response?
StealthLabs' experienced Cyber Incident Response Team (CIRT) uses a proven IR approach for advanced rapid cyber defense. Our approach includes:
1. Comprehensive Investigation
A comprehensive investigation of the incident is conducted to:
- Understand the severity of the incident
- Detect the compromised systems or networks
- Identify, preserve, and examine logs available for the incident
- Determine any critical systems or logs for further examination
- Identify if any immediate assessment is required
2. Assessing Damages
Assessing the damages caused by the incident helps in ascertaining the data exposed during the incident. It also helps in understanding what type of information the cybercriminals are looking for. We assess the damages by examining the:
- Files accessed
- Files potential or actually breached
- Immediate steps after the attack
3. Assist with IR Plan
Our incident handlers will assist you with an IR plan that addresses:
- Responsibility matrix in the event of a cyber incident
- Root cause analysis
- Remediation plan
Our Capabilities
When it comes to cyber incident response services, StealthLabs understands the broad set of capabilities enterprises need to enable end-to-end protection, from preparation to recovery. Our broad spectrum of Cyber Incident Response services enables your organization to access multiple specialist capabilities to help you before, during, and after an incident. These services include, but not limited to:

- 1. Cyber Incident Management
Efficient, coordinated, and structured management solution that helps reduce the impact of an incident. It includes workflow design, activity prioritization, IR team management, and high-level stakeholder communication. - 2. Malware Analysis
Analyzing known malicious software, executables, and scripts to understand their purpose and identify malicious activities through reverse engineering. - 3. Network and Endpoint Analysis
Analyzing networks and endpoints to detect and understand suspicious activity for indicators of compromise and active adversaries. - 4. Cyber Threat Intelligence (CTI)
Threat intelligence helps identify compromised data, malicious activity, or indicators of compromise relating to cyber incidents. - 5. Threat Hunting
Identify and resolve undetected and existing threats to accelerate remediation efforts promptly. Our team actively determines new attack patterns to identify attacks before they could cause potential damage. - 6. Incident Response Retainer
An incident response subscription service facilitates ready-to-use, 24/7 emergency incident response support from our skilled security team. - 7. Managed Detection and Response (MDR)
Managed threat detection and response provides a detailed picture of the cybersecurity environment to help detect endpoint attacks in real-time and disrupt them before they penetrate the enterprise assets. - 8. Incident Readiness Assessment
Our IR team helps conduct incident readiness assessment to baseline and benchmark your current readiness to respond, identify incidents, and make necessary improvements. - 9. Compromise Assessment
To help identify hidden compromised systems that may have bypassed your current security measures and enable remediation of events before they become incidents. - 10. Technology Recovery
Our Technology Recovery specialists help you enact contingency plans and return technical operations and systems to normalcy after an incident.
Why StealthLabs?
StealthLabs comprises highly skilled experts with decades of experience in leading-edge incident management, forensics, and security intelligence. We provide 24/7 remote and on-site IR assistance to rapidly contain and eradicate threats and limit the impact of the attack.
Based in Texas, StealthLabs is one of the leading Information Security Service and Solutions Providers in the US market. With years of industry presence and strong domain expertise, we have helped clients across various US states and cities plan, build and run successful cybersecurity programs.
